The escalating growth of malware on the Google Play Store is a cause for concern, with a significant portion of these malicious applications focusing on displaying ads and pilfering user credentials.
While the existence of malware targeting Android devices is not a new phenomenon, what is particularly surprising is the infiltration of such threats into the trusted Google Play Store. This vulnerability is attributed to the vast Android ecosystem, which boasts a staggering 2.5 billion active user devices.
This substantial user base positions Android as the largest operating system across all smartphones, creating an enticing target for cybercriminals. The sheer magnitude of 2.5 billion active devices underscores the immense challenge of safeguarding the Android platform from malicious activities.
List Of Malicious Apps On Google Play Store
Dendroid

Dendroid Banner Screenshot via Symantec blog.
In 2014, cybersecurity company Symantec uncovered a malicious application on the Google Play store, identified as Dendroid malware. This sophisticated spyware aimed to infiltrate the Google Play platform, possessing capabilities such as downloading images from the target device, blocking received SMS messages, recording calls, and more.
The discovery of Dendroid highlighted the evolving landscape of cyber threats, emphasizing the importance of robust security measures to protect users from increasingly sophisticated and invasive malware on widely-used platforms like Google Play.
Camera Vision Nocturna
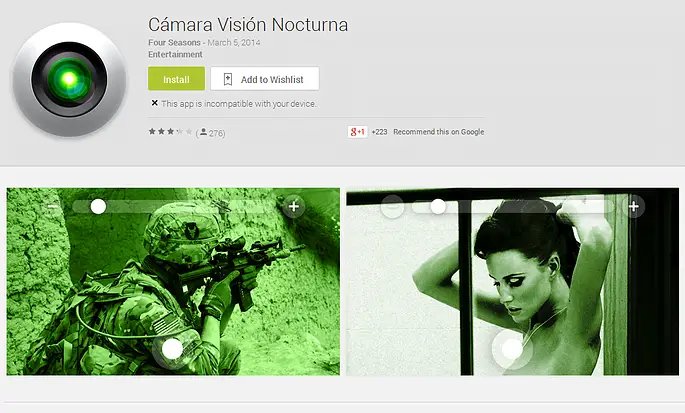
Camera Nocturna Apps Screenshots via Avast blog.
In 2014, Avast detected a deceptive malware application on the Google Play store called Camera Vision Nocturna. Disguised as a night vision camera app, this malware operated covertly to pilfer contact numbers from popular messaging platforms like WhatsApp, Telegram, or ChatOn.
Unbeknownst to users, it also surreptitiously subscribed them to premium messaging services, resulting in unauthorized charges that could go as high as $50.
This discovery underscored the need for users to exercise caution while downloading apps, emphasizing the importance of robust security practices to thwart malicious activities in the ever-evolving landscape of mobile threats.
Trojan AsiaHitGroup
One of the AsiaHitgroup as Google Play Store malware apps, Screenshot via Malwarebytes Blog.
In 2017, Malwarebytes exposed a cluster of Play Store malware applications named Asiahitgroup.
Disguised as seemingly harmless utility apps, including alarm clocks, QR scanners, compasses, photo editors, file explorers, and internet speed test apps, these applications were, in fact, trojans. Initially appearing innocent, they would stealthily disappear from the user’s view and prove nearly impossible to uninstall without a dedicated malware removal tool. If left unaddressed, the malware persisted by inundating the victim’s device with unwanted ads, underscoring the critical importance of vigilance and robust cybersecurity practices in the face of evolving mobile threats.
Expensive wall

ExpensiveWall Google Play Store Malware apps, Screen Shot via Checkpoint blog.
In 2017, Checkpoint security identified another insidious Google Play store malware masquerading as a Wallpaper app—Expensive Wall. Similar to previous threats like Camera Vision Nocturna, this malware clandestinely enrolled its victims in premium SMS services, resulting in unauthorized charges to the user’s account.
Remarkably pervasive, Expensive Wall infected 50 apps and was downloaded a staggering 4.2 million times, underscoring the alarming reach and potential impact of such malicious applications.
This revelation served as a stark reminder of the need for heightened security measures and user awareness when downloading seemingly innocuous apps from popular platforms like Google Play.
Luxury Car and Truck Simulation
In 2018, Forbes reported that Lukas Stefanko, an Android malware researcher, revealed a concerning incident.
More than 560,000 users were deceived into downloading a seemingly harmless Truck Simulation app on the Play Store.
Operating as Google Play store malware, these apps deviated from their purported functionality, remaining hidden while surreptitiously bombarding victims’ devices with unwanted ads.
This revelation emphasized the persistent threat of malware infiltrating trusted platforms, urging users to exercise caution and rely on vigilant security practices to safeguard their devices from such deceptive applications.
Latest Malware on Google Play Store (2019)
BeiTaAd
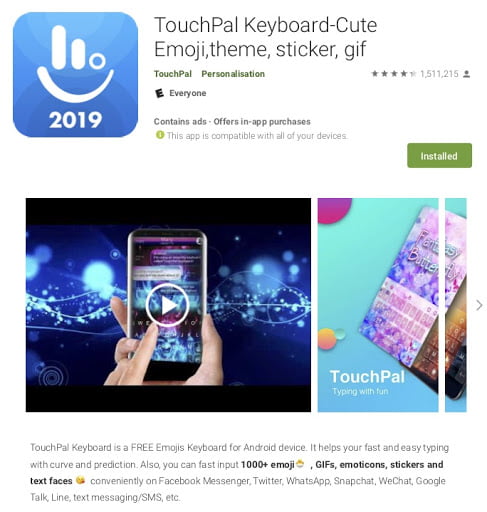
TouchPal keyboard infected by BeiTaAd, Screenshot via Lookout Security.
In June 2019, Lookout security company uncovered a new Google Play Store malware, BeiTaAds, embedded within the popular TouchPal keyboard.
This adware, initially concealed after installing TouchPal, activates its malicious activities after a few days. BeiTaAds then inundates users with relentless ads, rendering the device almost unusable.
TouchPal users reported extreme intrusiveness, with ads persistently popping up, hindering essential functions like answering calls.
Even on the lock screen, the malware’s continuous pop-ups disrupted normal device usage. This discovery highlighted the evolving sophistication of malware, emphasizing the need for heightened security measures to counter such intrusive threats.
Pink Camera Malware
In 2019, Kaspersky unveiled a Google Play Store malware called Pink Camera, identified as a particularly menacing backdoor malware. This type of malware is among the most perilous, as it grants attackers complete control over the victim’s device, leaving it vulnerable to manipulation.
Pink Camera operates deceptively, presenting itself as a semi-functional photo editing app with decent performance.
This camouflage ensures that victims do not immediately suspect it is malware. However, behind the scenes, the app discreetly steals valuable information such as phone numbers.
This pilfered data is then exploited to enroll victims in premium services, resulting in unauthorized monthly charges.
The discovery of Pink Camera highlighted the need for constant vigilance against seemingly innocuous apps and reinforced the importance of robust cybersecurity practices in the evolving landscape of mobile threats.
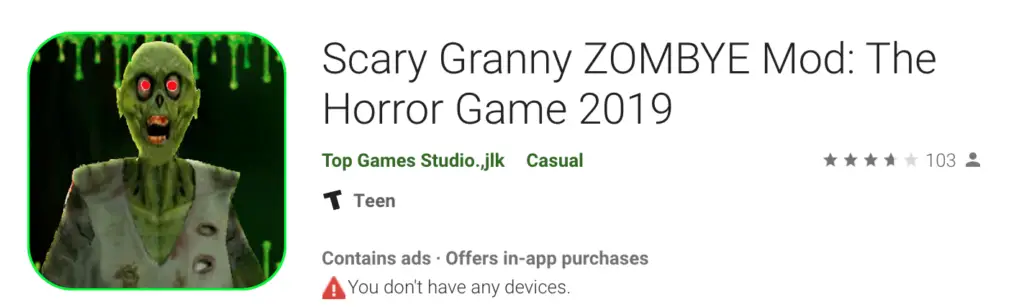
Scary Granny Zombie Mods Apps
The Scary Granny apps, Google Play Store Malware, Screenshot via Wandera.
In 2019, a Google Play Store malware came to light, detected by Wandera security research. This malicious application masqueraded as a fully functional horror game, initially exhibiting no signs of malicious activity. However, after a two-day grace period, the app revealed its nefarious intentions.
The malware was initiated by checking the Android version on the device. If the device ran a newer Android version, the malware refrained from any malicious attempts.
Conversely, for devices with older Android versions, the malware unleashed its harmful capabilities. This strategic differentiation stems from the fact that newer Android versions are generally more secure.
Upon assessing the Android version, the malware embarked on a phishing attack. Users would receive a notification urging them to update the Google Security Service. Subsequently, a fake Google Login interface would appear, surreptitiously stealing the victim’s username and password.
According to Wandera, the malware could also pilfer additional credentials such as recovery email, recovery phone numbers, birthdays, verification codes, cookies, and tokens.
Adding to its deceptive tactics, the malware could secretly display ads in the background, creating an illusion of open apps like Facebook and Amazon. In reality, these were ads cleverly disguised as legitimate applications, with the ominous presence of “Scary Granny.”
What makes this malware particularly alarming is its seamless integration within the fully functional game.
Victims could engage in gameplay with a polished interface, making it evident that the developer invested considerable effort to make the game appear innocuous, leaving unsuspecting users unaware of the underlying threat.
Bottom Line
The surge in malware on the Play Store shows no signs of abating, primarily driven by the motive of profit.
Advertisements, being a lucrative avenue, become a focal point for these malicious entities. While ads themselves are not inherently illegal and can serve positive purposes, their exploitation for malicious activities poses a significant threat.
A consistent pattern emerges from the previously discovered malware on the Play Store, with a shared strategy of stealing credentials and inundating users with pervasive ads.
While the malware mentioned in this account has been uncovered and removed from the Play Store, it’s crucial to acknowledge the persistent possibility of hidden malware. Remaining vigilant and cautious is imperative to mitigate the risks associated with potentially harmful applications. Stay aware, stay vigilant!